I suppose if I’m honest, I enjoy complex home network configurations, just for the sake of them. Not to make it difficult to use at all. It should be secure, yet simple.
A couple of years ago I ran across Astaro, recently acquired by Sophos. In short, it’s a Linux appliance that acts as a firewall between your network and your Internet connection. You need a spare computer to use it, unless you’re a corporation and want to shell out some cash to purchase their hardware appliance. You can also run it in a VMware environment, which I am doing. It behaves quite well and has given me zero issues. In a later post I’ll talk about my VMware environment specifically.
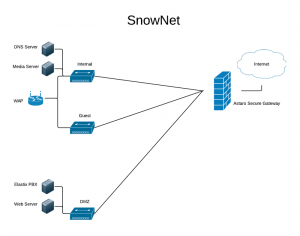 My home network isn’t terribly complex, but it isn’t your typical one either. The diagram to the right summarizes it pretty well (click it to enlarge).
My home network isn’t terribly complex, but it isn’t your typical one either. The diagram to the right summarizes it pretty well (click it to enlarge).
I have my DSL modem in bridged mode so that the connection from my firewall has my ISP’s assigned IP address so that I could avoid having my DSL modem doing a NAT in addition to my firewall. For my ISP, I can use Sophos UTM’s built-in PPPoE configuration to authenticate.
Behind my firewall, I have 3 different subnets. My main, ‘Internal’ one, a Guest network (to keep them separate from any other internal resources I’d prefer they not have access to), and a DMZ for any services I’d like to access from the Internet.
The ‘Internal’ subnet is where pretty much everything I use goes. Apple TVs, laptops, tablets, smartphones, printers, you name it. I have a media server running as a VM that serves my music, movies and home videos to devices throughout my home. I also have my own internal DNS server running on Linux that sits on my Internal subnet. I use it to access internal resources by name within my network.
The ‘Guest’ subnet is just what it would seem. A guest in my home can attach to it and get to the Internet. Besides having a port opened for DNS traffic to my DNS server internally, its only access is to the Internet.
The ‘DMZ’ subnet keeps things separate for services I’d like to access from the Internet. I have a web server I tinker with, as well as an Elastix-based PBX server for me to play with VOIP. Both of these are secure, but if a vulnerability was ever discovered and taken advantage of, the damage would be limited to the DMZ subnet. I have a firewall port open for DNS traffic to my internal DNS server, and then only services that I need. For instance, both servers use HTTP out to the Internet to download and install patches and updates, so I have that open. Otherwise, I only have ports open from the Internet to each of those servers to allow the connections I need for VOIP and web.
This is just an introduction to what I’ve done with my home network. In later posts, I’ll get into more detail on:
- VMware
- Sophos UTM
- VPN
…and how they all fit together in my network.